Generally there are two kinds of ransomware that you could be facing for which simply rebooting your machine or clearing your browser cache isnt an immediately viable solution. If you receive a bitcoin ransom email at your work email address report it immediately and follow the instructions given to you.
 Complete Guide To Ransomware How To Recover And Prevent An Attack
Complete Guide To Ransomware How To Recover And Prevent An Attack
Consider these anti-ransomware protocols.
What to do with ransomware email. Most ransomware attacks are initiated by phishing emails sent out to hook victims says Bastable. Use a password manager. If you already have a.
Avira Free Antivirus inklusive Ransomware-Schutz. Most Windows machines let you roll back the state of. When the computer restarts run antivirus software to remove the ransomware.
Password managers can keep a list of not just your passwords but also what site youve used them on the username you use to log in to that site any security questions you use on that site etc. As soon as you recognize that an email can possibly be ransomware or contains ransomware quickly take a screenshot of it for future reference and to have evidence of the email when reporting to authorities. Screen lockers can as their name suggests lock your screen.
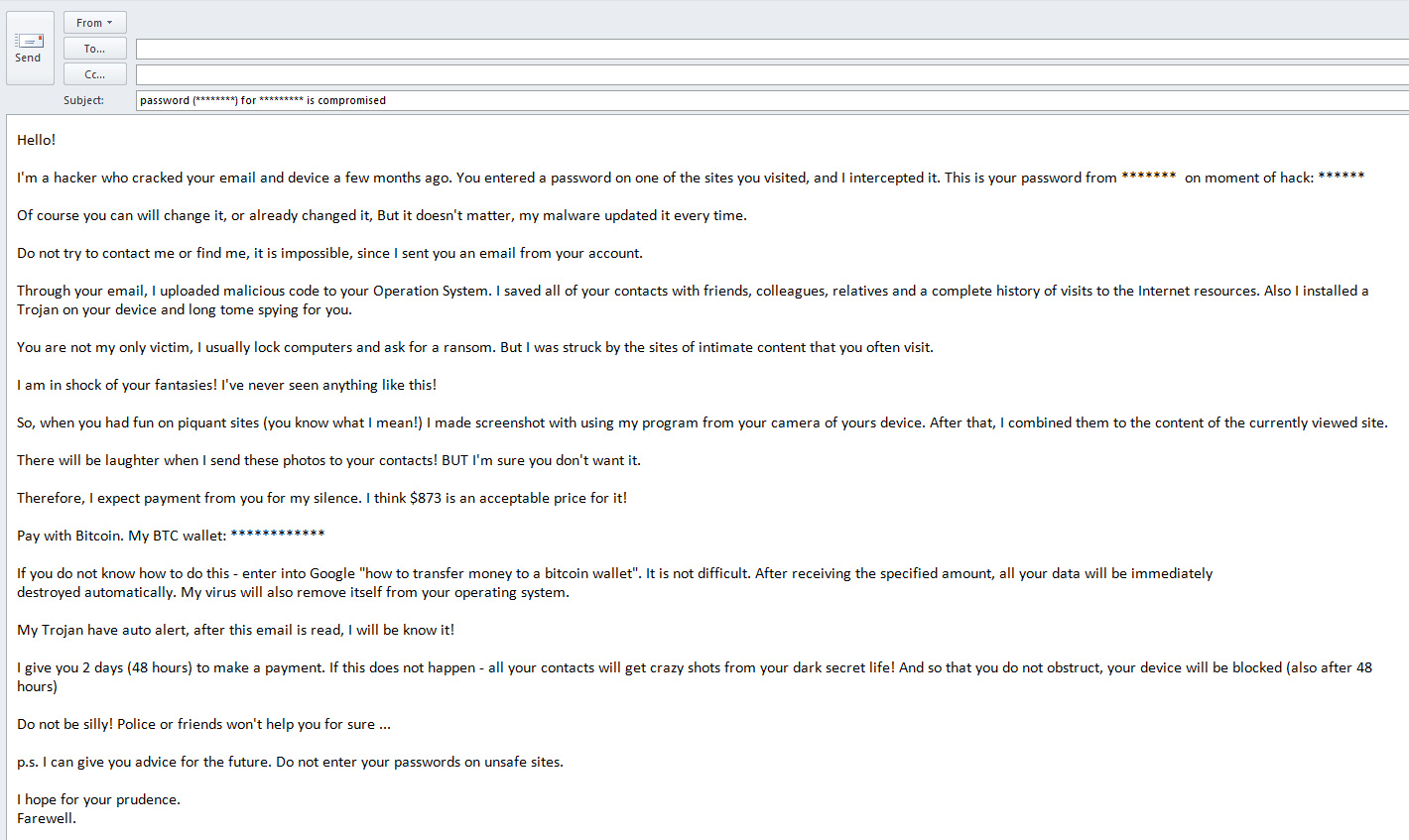
9 If the Ransomware totally blocked access to your computer or even restricted access to select important functions use Kaspersky WindowsUnlocker as it can clean up a ransomware infected. In the case of blackmail with the e-mail containing our password paying the ransom does not serve any purpose since the blackmailer does not have our data unless of course the password was not the current one and may not have gone to download the content of our e-mail box. Since ransomware is so expensive and disruptive your best line of defense is to prevent infection of your computer system in the first place.
If you receive the email to your personal email address mark it as Spam and delete it immediately. Phishers will try to trick employees into installing malware or gain intelligence for attacks by claiming to be from IT. Ideally you do not wait until you are suffering a ransomware attack to read guidance like this but build a set of your own in advance that is specific to your organisation.
You can unknowingly download ransomware onto a computer by opening an email attachment clicking an ad following a link or even visiting a website thats embedded with malware. Once the code is. Scareware is the least worrisome and essentially just attempts to scare users into paying a ransom but cant do anything more than annoy them with popups if they dont.
Train employees to be careful with emails. Once youve done that take the opportunity to make sure that your operating system and web browser are fully updated. Anzeige Free-Antivirus schützt vor Viren Ransomware Malware Co.
This guide offers you 5 top tips on how best to avoid ransomware in your email which is a common way for extortion-based malware to propagate itself. There are many more steps detailed and good advice offered in the full MS-ISAC Ransomware Guide and I would strongly recommend it to anyone responsible for securing an organisation against an attack. Now familiar and new forms of ransomware are using it again.
Do not forward the email unless you are asked to do so. Delete the email permanently. Once you recognize that an email may be ransomware immediately run your anti-malware scanners to be sure.
Do not provide personal information when answering an email unsolicited phone call text message or instant message. A password manager is a program designed to remember your passwords for you. Avira Free Antivirus inklusive Ransomware-Schutz.
Be sure to contact your IT. The three main types of ransomware include scareware screen lockers and encrypting ransomware. Email was once the main method for delivering ransomware.
Try System Restore if Safe Mode doesnt work. Anzeige Free-Antivirus schützt vor Viren Ransomware Malware Co.
 Ransomware Information Services Queen S University Belfast
Ransomware Information Services Queen S University Belfast
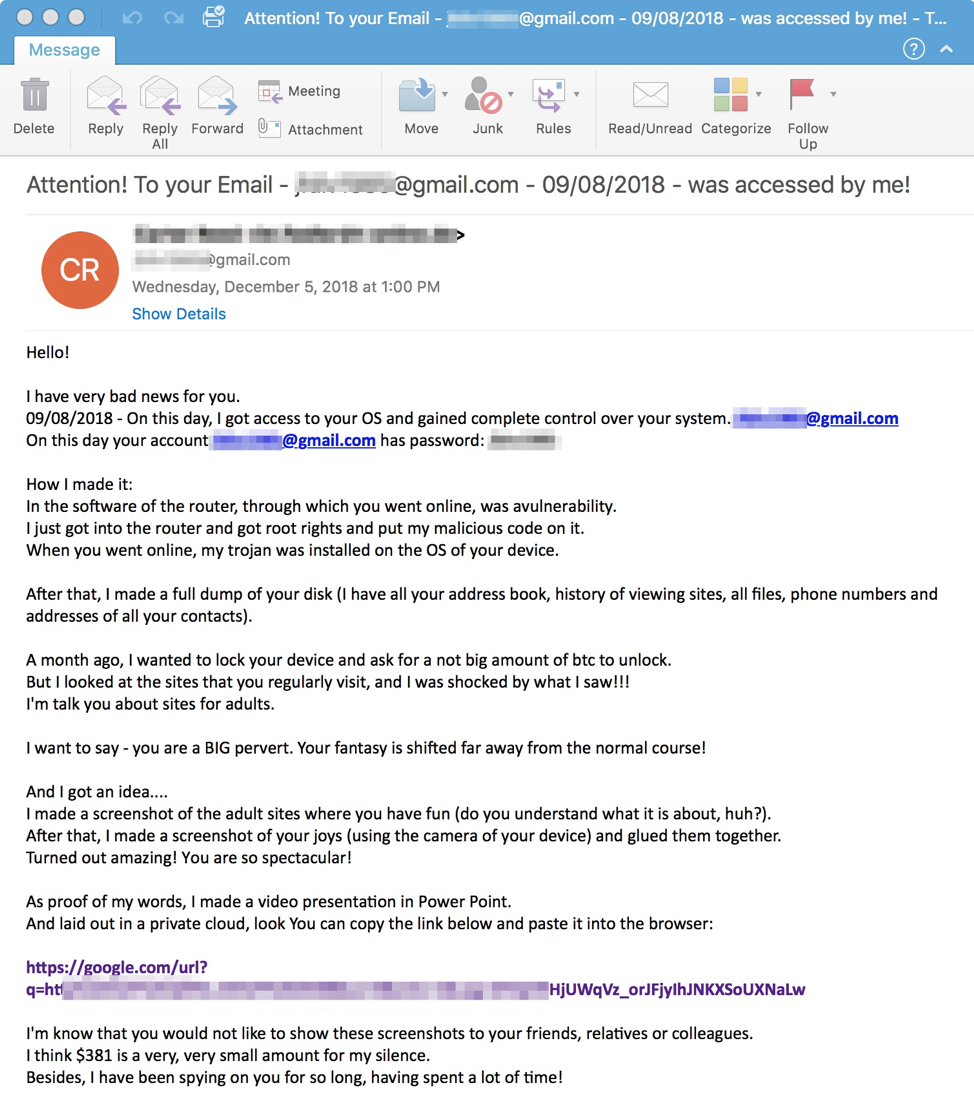 Sextortion With A Side Of Ransomware Proofpoint
Sextortion With A Side Of Ransomware Proofpoint
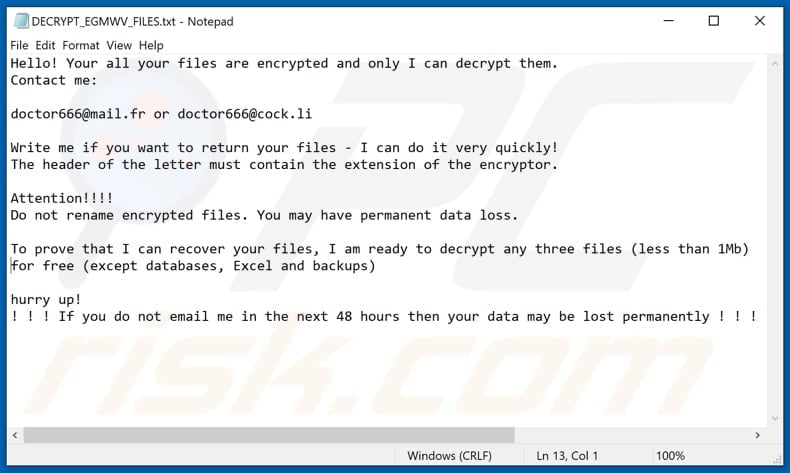
 How To Remove Doctor666 Ransomware Virus Removal Steps Updated
How To Remove Doctor666 Ransomware Virus Removal Steps Updated
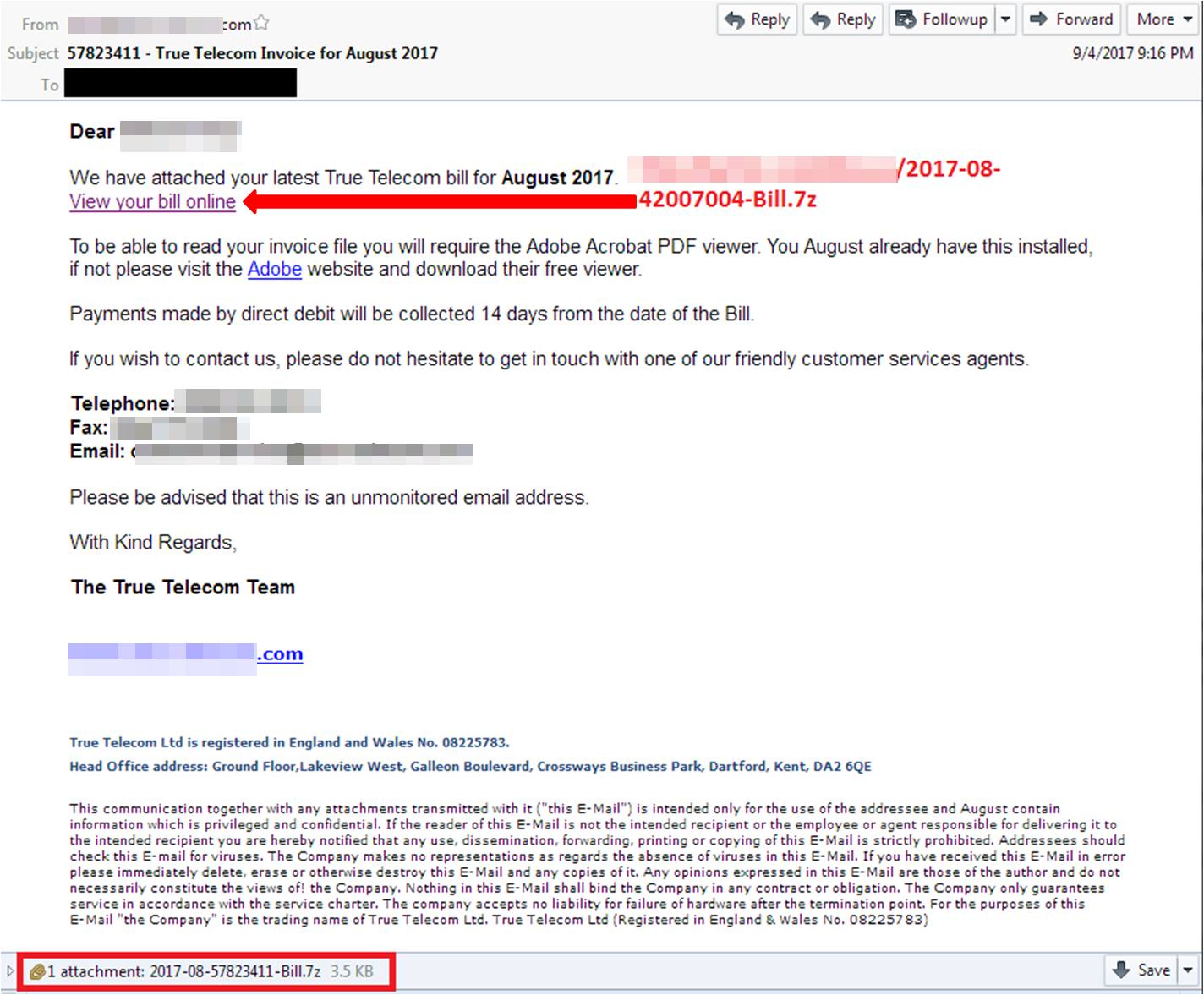 Ransomware Recap Crypshed Spoofs Amazon In Ransomware Campaign Noticias Sobre Seguranca Trend Micro Br
Ransomware Recap Crypshed Spoofs Amazon In Ransomware Campaign Noticias Sobre Seguranca Trend Micro Br
New Locky Ransomware Faqs And What To Do Now Dwp Information Architects
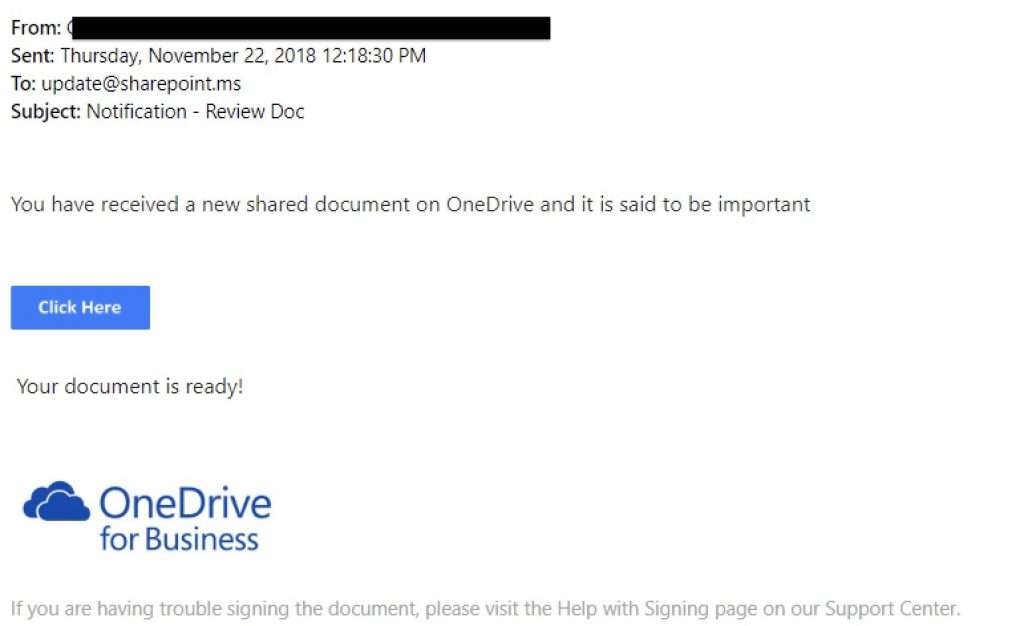 4 Ways Hackers Use Phishing To Launch Ransomware Attacks
4 Ways Hackers Use Phishing To Launch Ransomware Attacks
 Why You Need To Know About Ransomware Interpreting Technolgy
Why You Need To Know About Ransomware Interpreting Technolgy
How To Respond To A Sextortion Email Which Computing Helpdesk
 Why You Need To Know About Ransomware Interpreting Technolgy
Why You Need To Know About Ransomware Interpreting Technolgy
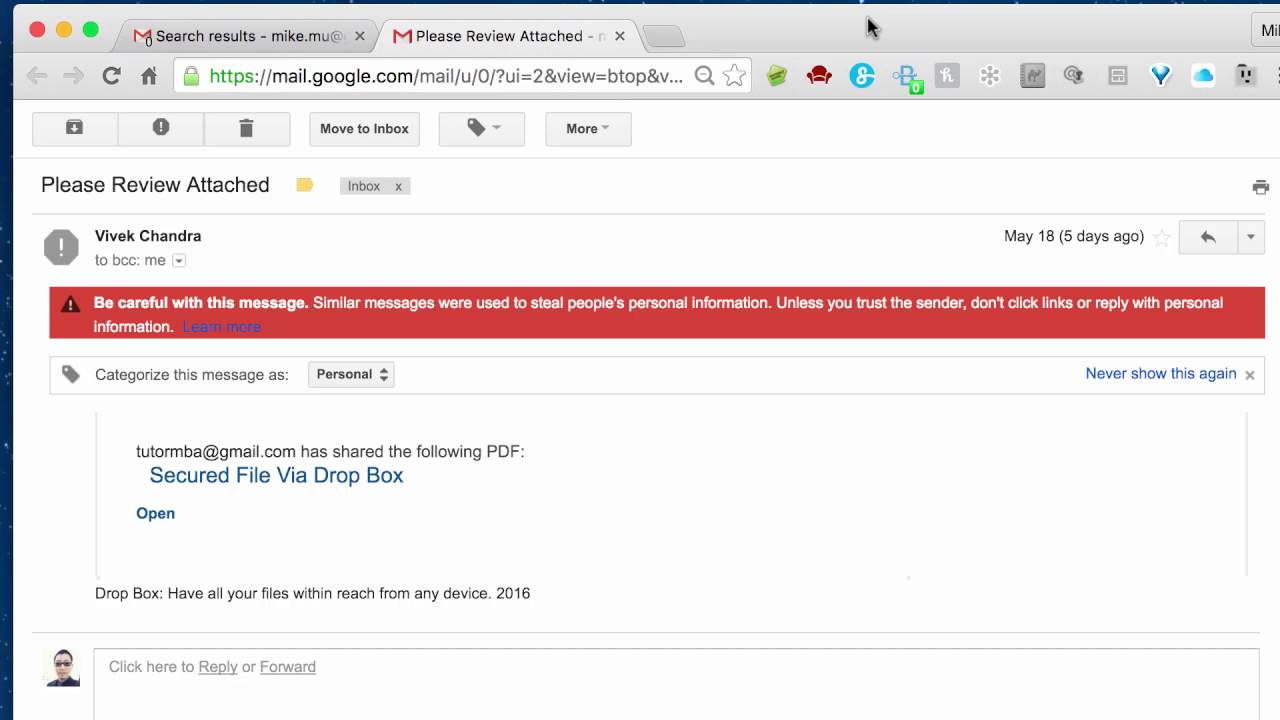 Ransomware Email Example 2016 May Youtube
Ransomware Email Example 2016 May Youtube
 Case Study Of Phishing For Data Theft Ransom Locky Ransomware Infosec Resources
Case Study Of Phishing For Data Theft Ransom Locky Ransomware Infosec Resources
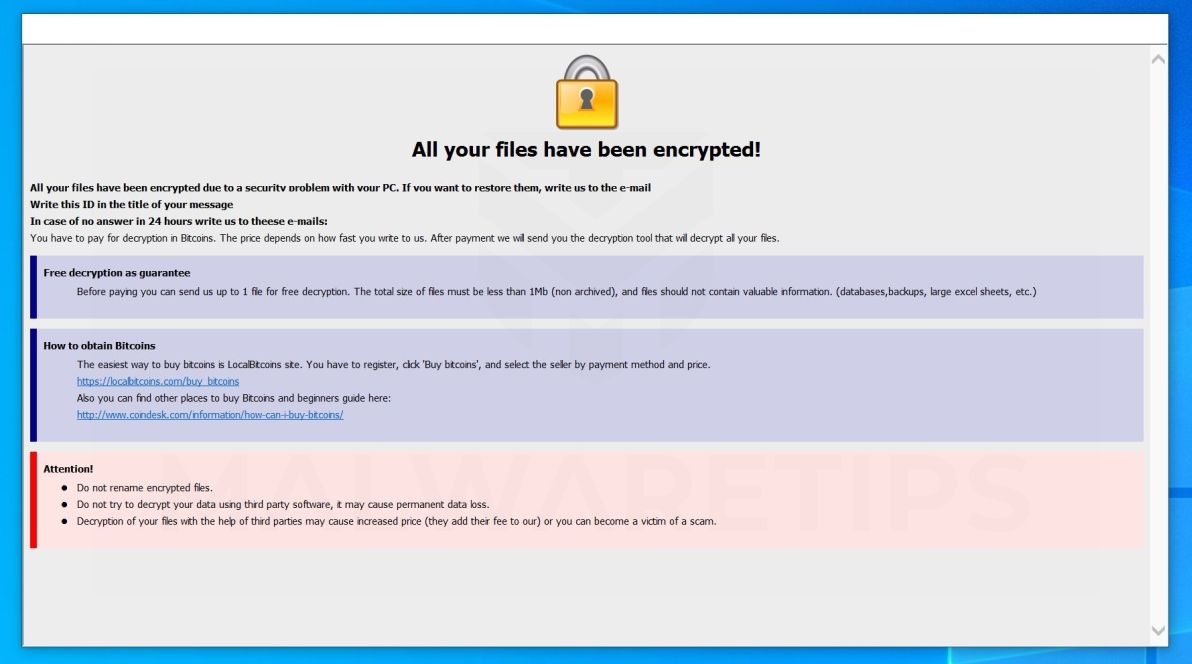 Remove Bitcoin Email Tg Ncov Ransomware Virus Removal Guide
Remove Bitcoin Email Tg Ncov Ransomware Virus Removal Guide

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.